Hello again !
After struggling a while longer, watching a bunch of tutorial videos, scouring the endless forum threads, and testing many things, I finally got my SSL Certificate to work !
The following tutorials helped me a lot :
- https://www.youtube.com/watch?v=T4Df5_cojAs&ab_channel=kubucation
- https://deliciousbrains.com/ssl-certificate-authority-for-local-https-development/
- https://medium.com/@antelle/how-to-generate-a-self-signed-ssl-certificate-for-an-ip-address-f0dd8dddf754
If anyone is interested, these are the steps I followed (some commands might require sudo privileges):
** SSL Certificate
**** Create a Certificate Authority (CA)
openssl genrsa -des3 -out myCA.key 2048
openssl req -x509 -new -nodes -key myCA.key -sha256 -days 1825 -out myCA.pem
**** Create a private key pair for the web server
openssl genrsa -out odkcentral.key 2048
**** Generate a Certificate Signing Request (CSR)
openssl req -new -key odkcentral.key -out odkcentral.csr
**** Create a .ext configuration file for the server, with the following text
nano odkcentral.ext
----
authorityKeyIdentifier=keyid,issuer
basicConstraints=CA:FALSE
keyUsage = digitalSignature, nonRepudiation, keyEncipherment, dataEncipherment
subjectAltName = @alt_names
[alt_names]
IP.0 = 127.0.0.1
IP.1 = XXX.XXX.XXX.XXX
DNS.0 = localhost
DNS.1 = XXXXX.XXX
----
**** Generate a server Certificate from the CSR + CA key pair
openssl x509 -req -in odkcentral.csr -CA myCA.pem -CAkey myCA.key -CAcreateserial -out odkcentral.crt -days 1825 -sha256 -extfile odkcentral.ext
**** Copy server certificate, server key and CA public key
**** Add to ODK Central project, in the nginx configuration
cp odkcentral.crt <central/files/local/customssl>
cp odkcentral.key <central/files/local/customssl>
cp myCA.pem <central/files/local/customssl>
**** Change nginx host configuration files to point to these files
- ssl_certificate /etc/${SSL_TYPE}/live/${CNAME}/fullchain.pem;
- ssl_certificate_key /etc/${SSL_TYPE}/live/${CNAME}/privkey.pem;
- ssl_trusted_certificate /etc/${SSL_TYPE}/live/${CNAME}/fullchain.pem;
+ ssl_certificate /etc/${SSL_TYPE}/live/${CNAME}/odkcentral.crt;
+ ssl_certificate_key /etc/${SSL_TYPE}/live/${CNAME}/odkcentral.key;
+ ssl_trusted_certificate /etc/${SSL_TYPE}/live/${CNAME}/myCA.pem;
**** Change nginx dockerfile copy statement to copy all files, not only .pem
-COPY files/local/customssl/*.pem /etc/customssl/live/local/
+COPY files/local/customssl /etc/customssl/live/local
I'm not sure if the last 2 steps are really necessary, or if the .crt renamed as fullchain.pem and .key file renamed as privkey.pem would have done the trick. Maybe I will test this later and edit the post.
So when I install this new certificate on my Windows PC client (see instructions here) I could see my website at safe.
This works when typing the IP address in the search bar, and also with the domain name I got from FreeDNS.
HOWEVER I still have some problems with Enketo and the ODK Collect app.
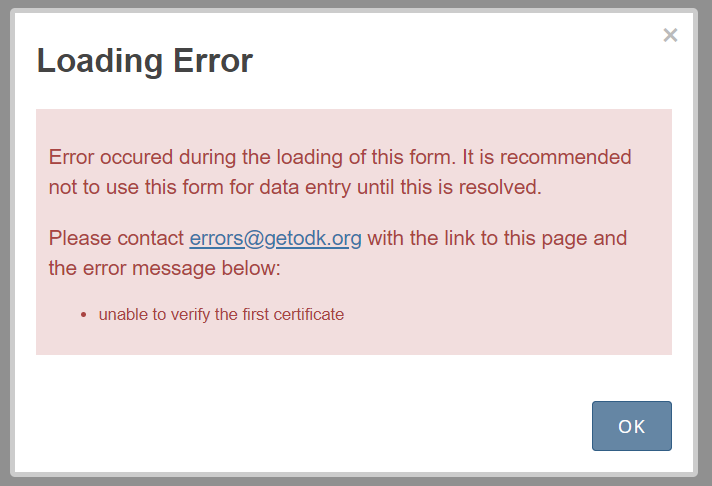
In Enketo, I get the following error message:
Is there a way to make Enketo work with the customssl setup on a local network ? Did someone manage to do this ?
On the ODK Collect App (on a Huawei, Android 8), I can't get my blank forms, no error message is displayed, just a very short loading screen and then nothing.
But I have installed the certificate on my Huawei phone, and I can access the web application through the Chrome browser.
I will try the solution @dmenne suggested, in this post, and check if that works. (but I need to install Android Studio, get the code, etc .. first).
Anyway thanks already for your help, I am moving forward, even though not everything works yet...
Jonathan